The Proxy Pattern: A Structural Pinnacle in Software Design
In the vast realm of structural design patterns, where software components are meticulously orchestrated to create harmonious systems, the Proxy Pattern emerges as a cornerstone. Serving as an intermediary or a stand-in for another object, the Proxy Pattern exemplifies encapsulation, control, and advanced coupling, core tenets of sound software design.
Definition of Proxy Pattern
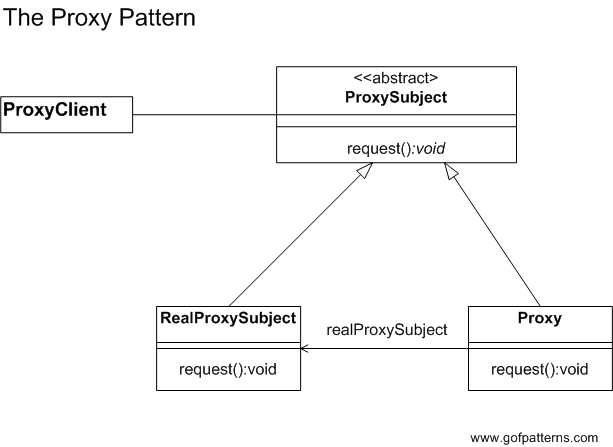
The Proxy Pattern provides a surrogate or placeholder for another object to control access to it. In essence, instead of interacting directly with the original object, a client interacts with a proxy, which then determines whether, how, and when to forward these interactions to the underlying object.
Key Roles within the Proxy Pattern
- Proxy: This is the intermediary that represents the real object. It controls access to the real subject, managing the creation, maintenance, and potential destruction of it. The proxy is often responsible for tasks such as lazy initialization, logging, access control, and computation-intensive operations that should be deferred until necessary.
- Real Subject: The actual object that the proxy represents. It defines the real logic or the genuine computational functionality which the proxy can defer to.
- Subject Interface: Both the Proxy and the Real Subject implement this, ensuring that the Proxy can be used interchangeably with the Real Subject.
Functions and Advantages of the Proxy Pattern
- Controlled Access: One of the primary benefits of the Proxy Pattern is the regulation of operations on the Real Subject. For instance, certain methods may require authentication, and the proxy can manage this before allowing operations to reach the Real Subject.
- Lazy Initialization: Often, creating an instance of the Real Subject can be resource-intensive. The proxy can defer this instantiation until it is absolutely required, thereby optimizing system resources.
- Logging and Auditing: Every request made through the proxy can be logged, allowing for an audit trail of operations performed on the Real Subject.
- Networked Distribution: In distributed systems, the Real Subject might exist in a different address space. The proxy can hide the intricacies of accessing a remote object, providing a local representation for remote resources.
- Reference Counting: In scenarios where resources are limited, the proxy can maintain a count of references to the Real Subject, enabling efficient memory management and potential deallocation when the object is no longer required.
Proxy Pattern within Structural Patterns
Structural design patterns primarily emphasize the composition of classes and objects, paving the way for larger systems that are scalable, maintainable, and efficiently structured. The Proxy Pattern fits seamlessly within this paradigm by emphasizing encapsulation, adding a layer of indirection, and fostering controlled access to critical system components. While other structural patterns like Adapter focus on interface reconciliation and Facade on simplifying interfaces, the Proxy Pattern prioritizes controlled access and representation.
The Proxy pattern provides a surrogate or placeholder object to control access to the original object.
There are several types of implementations of the Proxy pattern with the
There are several types of implementations of the Proxy pattern with the
- Remote proxy and
- Virtual proxy
Problem Solution using the Proxy Pattern:
You are currently designing your own Desktop Publishing application, as you have not found any that do exactly what you want with existing applications.
As part of the design you are using a Controller to which you send all GUI requests.
Not all objects can process the same commands. For example you cannot select the spell check tool when an image has the focus.
To stop any possible errors you would like to filter out some of the messages as they are passed from these objects to the Controller object. What pattern could you use?
In this scenario what you are essentially trying to do is filter all packets that don't meet a certain set of requirements. This behavior is just like a Proxy server dropping packets from certain IP address etc.
Benefits of Proxy Pattern:
- A Remote proxy can hide the fact that an object resides in a different address space
- A virtual proxy can perform optimizations, such as creating an object on demand.
When to Use Proxy Pattern:
You should use the proxy pattern when:
You need a more versatile or sophisticated reference to an object than a simple pointer.
The Proxy Pattern, with its emphasis on controlled access, indirection, and efficient resource management, stands as an emblematic figure within the pantheon of structural design patterns. By ensuring that system components are accessed in a regulated and optimized manner, the Proxy Pattern significantly augments the robustness, efficiency, and modularity of software architectures.
You need a more versatile or sophisticated reference to an object than a simple pointer.
The Proxy Pattern, with its emphasis on controlled access, indirection, and efficient resource management, stands as an emblematic figure within the pantheon of structural design patterns. By ensuring that system components are accessed in a regulated and optimized manner, the Proxy Pattern significantly augments the robustness, efficiency, and modularity of software architectures.
Proxy Pattern Code